Monitor Microsoft Exchange Server on a remote Windows server | ActiveXperts Network Monitor
ActiveXperts solution to monitor Microsoft Exchange Server
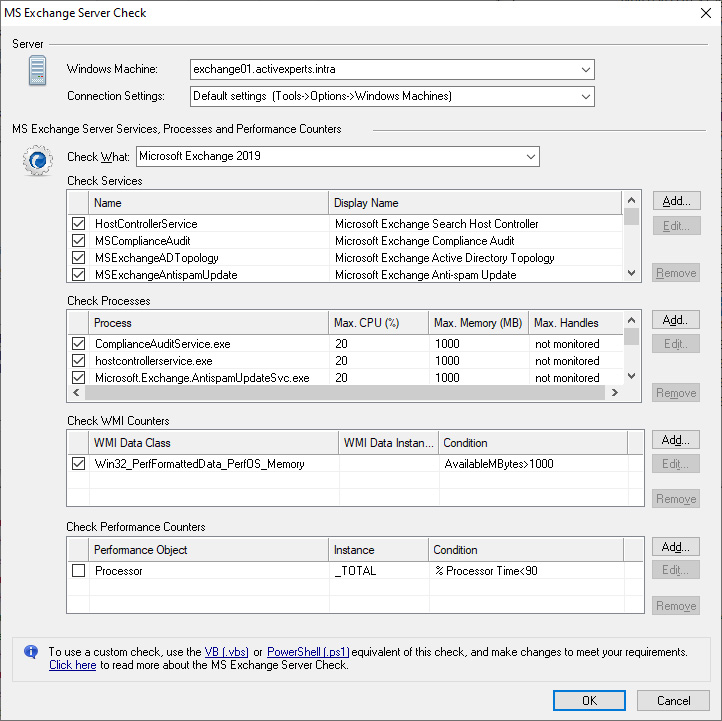
ActiveXperts Network Monitor monitors the status of the Exchange services, and monitors the most important performance counters. Among these performance counters are: performance counters for the Information Store, mailboxes, public folders and SMTP connector. If it drops too low you're notified immediately. One can extend the Exchange check function by checking more services and monitoring more performance counters. The following MS Exchange versions are supported: 2010, 2007, 2003, 2000 and 5.x.
An MS Exchange Server check requires the following parameters:
- Services - A list of MS Exchange Server services that should be running on the target server;
- Processes - A list of MS Exchange Server processes that should be running on the target server;
- Performance Counters - A list of MS Exchange Server performance counters that should be monitored;
- WMI Performance Counters - A list of MS Exchange Server WMI counters that should be monitored.
About MS Exchange
Exchange is the Microsoft messaging and collaboration server designed to help your business communicate more effectively. Along with the rich client functionality provided by Microsoft Office Outlook, Exchange offers mobile, remote, and desktop e-mail access with state-of-the-art security and privacy; lower cost of ownership through the services provided by Microsoft Windows Server; high reliability and outstanding performance; e-mail-based collaboration; and easy upgrading, deployment, and administration.
Exchange features the following:
- Distribution lists restricted to authenticated users. You can allow only sending from authenticated users or specify which users can or cannot send mail to specified distribution lists.
- Support of real-time Safe and Block lists. Reduce the amount of unsolicited mail delivered to your organization with connection filtering.
- Inbound recipient filtering. Reduce unsolicited e-mail messages by filtering inbound messages based on the recipient. Messages that are addressed to users that are not found, or to whom the sender does not have the permissions to send, are rejected. This applies only to messages sent by anonymously authenticated users.
- Kerberos authentication between a front-end and back-end server. To help ensure that credentials are secure, Exchange uses Kerberos delegation when sending user credentials between a front-end server, such as Microsoft Office Outlook Web Access or Outlook Mobile Access, and a back-end server such as the mailbox store.
- Privacy protection in Outlook and Outlook Web Access. By default, content from outside your network is blocked in Outlook and Outlook Web Access. This feature helps prevent spammers from identifying valid e-mail addresses through links to external content. You can, however, override this feature to view external content.
- Virus Scanning API. Third-party antivirus products can run on servers running Exchange that do not have resident Exchange mailboxes and are allowed to delete and send messages to the sender.
- Antispam integration with Outlook and Outlook Web Access. You can upload the Safe and Block Senders List to Exchange for filtering.
- Clustering security. Exchange clustering supports Kerberos authentication against an Exchange virtual server. Exchange also supports Internet Protocol security (IPSec) between front-end servers and clustered back-end servers running Exchange.
- Administrative permissions. Cross-forest support and the ability to administer both Exchange 2000/2003 and Exchange helps organizations that have segmented the administration of their Microsoft Windows based environment and Exchange environment into two unique groups and are concerned about security.
- Restricted relaying. You can restrict relaying to a limited number of security principles through the standard Windows 2000/2003 discretionary access control list (DACL). The ability to grant relaying to an IP address is still present.
- Restricted submissions. You can restrict submissions to a limited number of security principles through the standard Windows 2000/2003 DACL. This feature helps prevent blocked senders from sending to internal-only distribution lists by spoofing, which is the practice of tricking users into providing passwords and other information to allow unauthorized access into a system.
- Public folder permissions for unknown users. Folders with distinguished names in access control lists that cannot be resolved to security identifiers drop the unresolvable distinguished names.
- Public folder store replication. Public folder servers replicate with local servers for updates even if the local servers do not have the full set of replication content that they need. You can use a registry key to identify the first server that is used for backfilling. For more information, read the Exchange Security Enhancements white paper.